The 2025 Cisco Segmentation Report, with 1,000 respondents, was launched final month and has prompted me to assume extra deeply in regards to the evolution of the decades-old cybersecurity idea and the way it continues to adapt to fulfill the wants of contemporary enterprises. I beforehand wrote that whereas 79% of respondents contemplate segmentation a high precedence, solely 33% implement it absolutely. The survey outcomes additionally revealed fascinating insights into why segmentation stays a foundational idea.
The evolution of segmentation and the event of various segmentation approaches make the idea splendid for implementing a proactive strategy to enterprise cybersecurity in the present day. For years, organizations have utilized macro-segmentation to divide networks into smaller sections, which helps restrict the unfold of profitable assaults whereas enhancing total resilience. And now, augmenting macro-segmentation with micro-segmentation implementations permits safety groups to separate environments into separate networks AND isolate particular workloads based mostly on conduct or identification. This twin segmentation strategy is well-suited to guard in the present day’s distributed, cloud-first community infrastructure and the purposes, knowledge, and customers that depend on these vital networks.
That is the primary a part of a three-part sequence that delves deeper into the survey outcomes and what they reveal in regards to the present state of segmentation.
Macro-Segmentation (On It’s Personal) Is Not Sufficient to Meet At present’s Cybersecurity Challenges
Macro-segmentation alone is inadequate as a result of latest modifications in fashionable software structure. Trendy purposes are not monolithic, and they’re not constrained by a subnet or VLAN. Because of this, these purposes are decentralized and composed of a number of workloads. This new decentralized structure has boosted software efficiency, scalability, maintainability, and reliability; nonetheless, it has made it difficult to grasp what’s occurring on the workload degree.
Nonetheless, the shortage of visibility and management on the workload degree makes conventional safety approaches (together with macro-segmentation) difficult. It’s no surprise that cybersecurity groups are struggling to guard in the present day’s extremely distributed, cloud-first digital infrastructures.
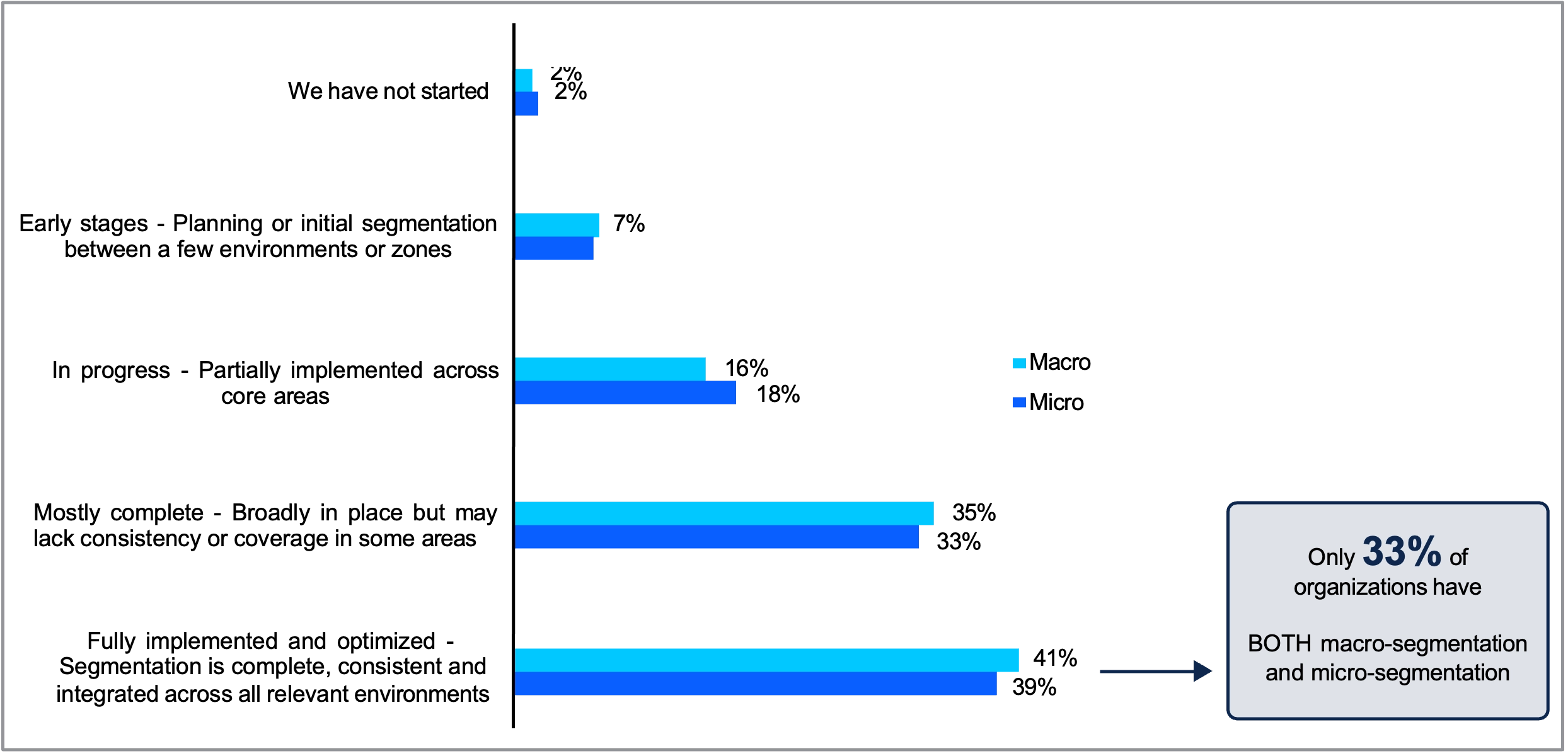
Organizations Must Implement Macro-Segmentation and Micro-Segmentation in Tandem
Augmenting macro-segmentation with micro-segmentation implementations permits safety groups to separate IT environments into sections whereas isolating particular person workloads based mostly on their conduct or identification. This allows a proactive strategy to cybersecurity, leading to sooner restoration instances, improved operations, and constant enforcement of segmentation insurance policies.
1. Faster Restoration Occasions
Respondents from organizations which have absolutely carried out each macro- and micro-segmentation report that breach containment and restoration take a median of 20 days to finish. In distinction, respondents from organizations that haven’t absolutely carried out each macro- and micro-segmentation report that restoration takes them a median of 29 days.
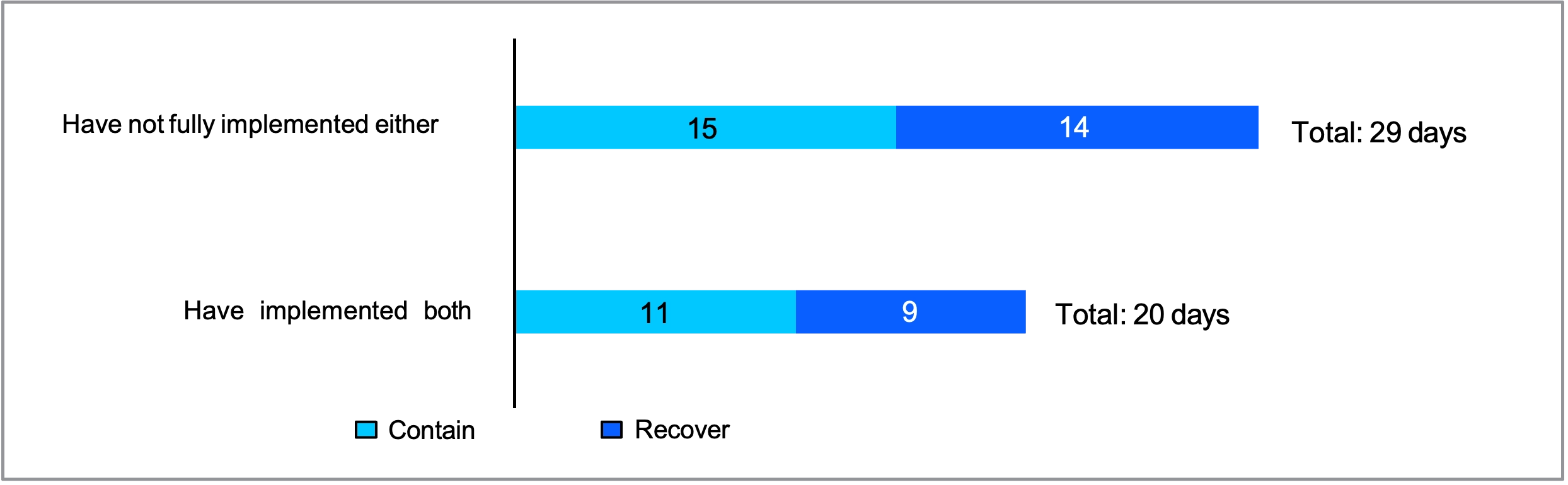

This can be a huge, huge deal. Reducing restoration time by one-third limits the breach’s impression and prevents its future unfold. Simply think about the injury that risk actors can inflict in these extra 9 days. The mixture of macro- and micro-segmentation slows down attackers. It additionally gives defenders with extra visibility and management over particular person workloads, providing insights into the assault chain that allow them to shortly establish which property must be quarantined, taken offline, and recovered.
2. An Alternative to Align Groups
Segmentation initiatives require coordination throughout a number of groups with a number of layers of duty, necessitating full alignment all through the group. For instance, a improvement group is aware of who created an software, however it could not have visibility into who’s utilizing the appliance or how the appliance is getting used. A failure to coordinate throughout groups can result in over-permissioning—a typical mistake that creates important dangers for organizations.
In accordance with the survey, organizations (typically) depend on three separate groups for implementing and managing segmentation—IT infrastructure or community (87%), Safety/ SecOps (77%), and DevOps/ Cloud Engineering (71%). The method of implementing each macro- and micro-segmentation can enhance alignment between these groups and remove a lot of the danger related to over-permissioning. Persevering with with our improvement group instance, the drive towards segmentation can convey the event group nearer to these managing and securing the community by establishing a typical vocabulary and shared aims.
Amongst survey respondents at organizations which have absolutely carried out each macro- and micro-segmentation, 87% report that their groups are absolutely aligned, in contrast with 52% of these at organizations with out full implementation.
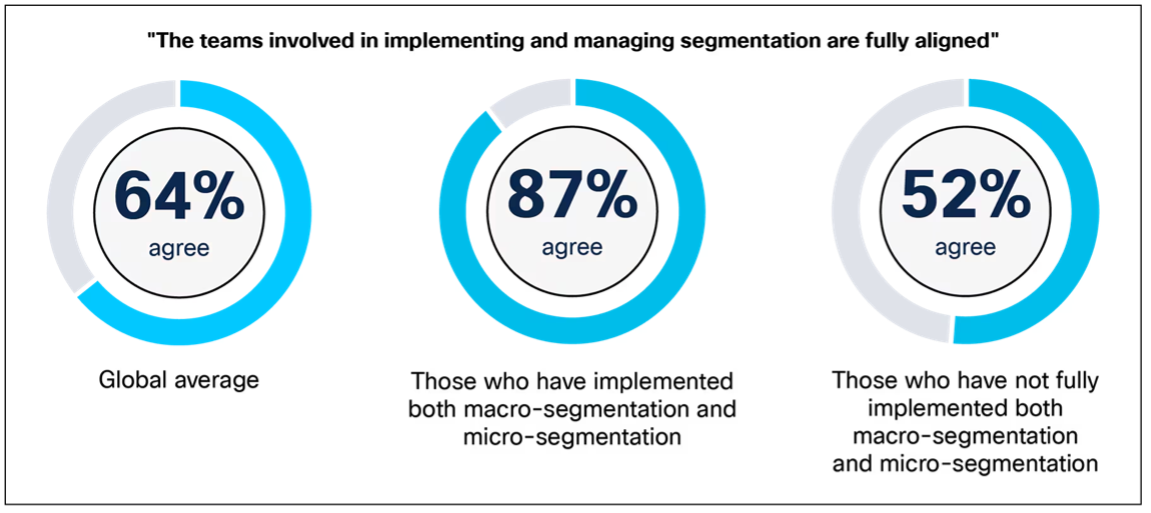

3. Constant Enforcement
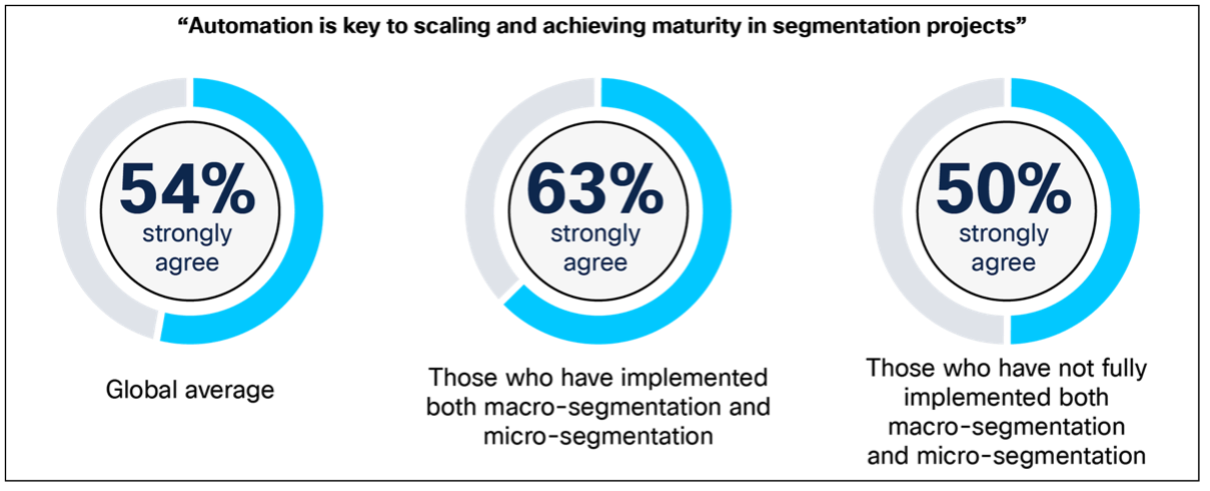
In accordance with the report, two-thirds (63%) of respondents at organizations with full implementation strongly agree that automation is vital to scaling and maturing segmentation initiatives, versus 50% with out full implementation of each. Automation permits organizations to scale their segmentation insurance policies throughout all the group (or at the very least the place it is smart), leading to extra complete and constant enforcement, and in the end, stronger safety controls. Organizations that don’t make use of satisfactory automation should manually create and preserve insurance policies, which might simply fall behind safety necessities over time.

A Twin Strategy Allows a Proactive Cybersecurity Technique
The flexibility to implement micro-segmentation at scale together with macro-segmentation has change into foundational to fashionable enterprise safety methods and the zero-trust safety mannequin. This allows organizations to get well extra shortly, higher align their groups, and implement segmentation extra persistently—together, permitting for a proactive strategy to cybersecurity. Though segmentation is an outdated idea (from an IT perspective, in fact), it stays a vital element of a proactive enterprise safety strategy—primarily as a result of its adaptation for contemporary environments.
In my subsequent weblog, I’ll define the challenges organizations are dealing with in the present day when implementing segmentation initiatives. Within the meantime, obtain the 2025 Cisco Segmentation Report to raised perceive the state of segmentation in the present day.
We’d love to listen to what you assume! Ask a query and keep linked with Cisco Safety on social media.
Cisco Safety Social Media

