Introduction
I not too long ago wanted to poke round an APK. I would carried out this form of factor earlier than, however it’s been years so the method of organising an Android surroundings was unfamilar. As a substitute of spending a day reimmersing myself for what was (hopefully) going to be a 10-15 minute factor, I turned to a different device: Cellular Safety Framework (often known as MobSF)
Establishing Docker
There are numerous weblog posts, articles, and YouTube movies on the best way to arrange the proper docker surroundings. This was a fast job. I did not want “excellent”, I wanted adequate. On the time, I used to be on a Home windows 11 machine, so that is what I needed to work with. The aim was to get Docker operational as shortly as potential.
Why? MobSF has a fast setup with two strains of Docker code.
Utilizing the Set up Docker for Home windows documentation, I downloaded the installable and began the method. The set up took a pair minutes on the machine I used to be on and required me to sign off and again in. Whole set up time was lower than 5 minutes.
Putting in MobSF
As soon as logged again in, I fired up the command line. The MobSF README supplies two strains to execute on the command line to drag the most recent picture. I did not undergo the method of organising a dymanic analyzer. I did not suppose I would want it (and as luck would have it on this case, I used to be appropriate).
Run the 2 instructions:
docker pull opensecurity/mobile-security-framework-mobsf:newest
docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:newest
This can pull the most recent model of MobSF after which run it on port 8000 on the native machine. As soon as it is operating you possibly can entry it in your browser by going to http://127.0.0.1:8000
Discover your APK
Theorectically, you may be operating this in opposition to an APK you have constructed and developed. In that case, you may have the APK useful and might load it into the UI. I, sadly, did not have that luxuary. Luckily, getting the APK is comparatively easy.
- Go to the Google Playstore and seek for the appliance
- Navigate into the small print web page of the appliance (it’s best to see the choice to put in it)
- Copy the URL to this web page
- Go to APKCombo
- Paste the URL you copied in step 3 instal the suitable textual content field and click on “Generate Obtain Hyperlink”
- After a couple of seconds, click on the obtain icon subsequent to the hyperlink that was generated
You now have the APK to make use of.
Utilizing MobSF
With the APK in hand, and MobSF operating, navigate to http://127.0.0.1:8000. Add the APK and wait a few minutes. If you’re watching the logs, you may see it performing a number of steps behind the scenes. As soon as it is carried out analyzing the APK, it’s going to drop you to the dashboard.
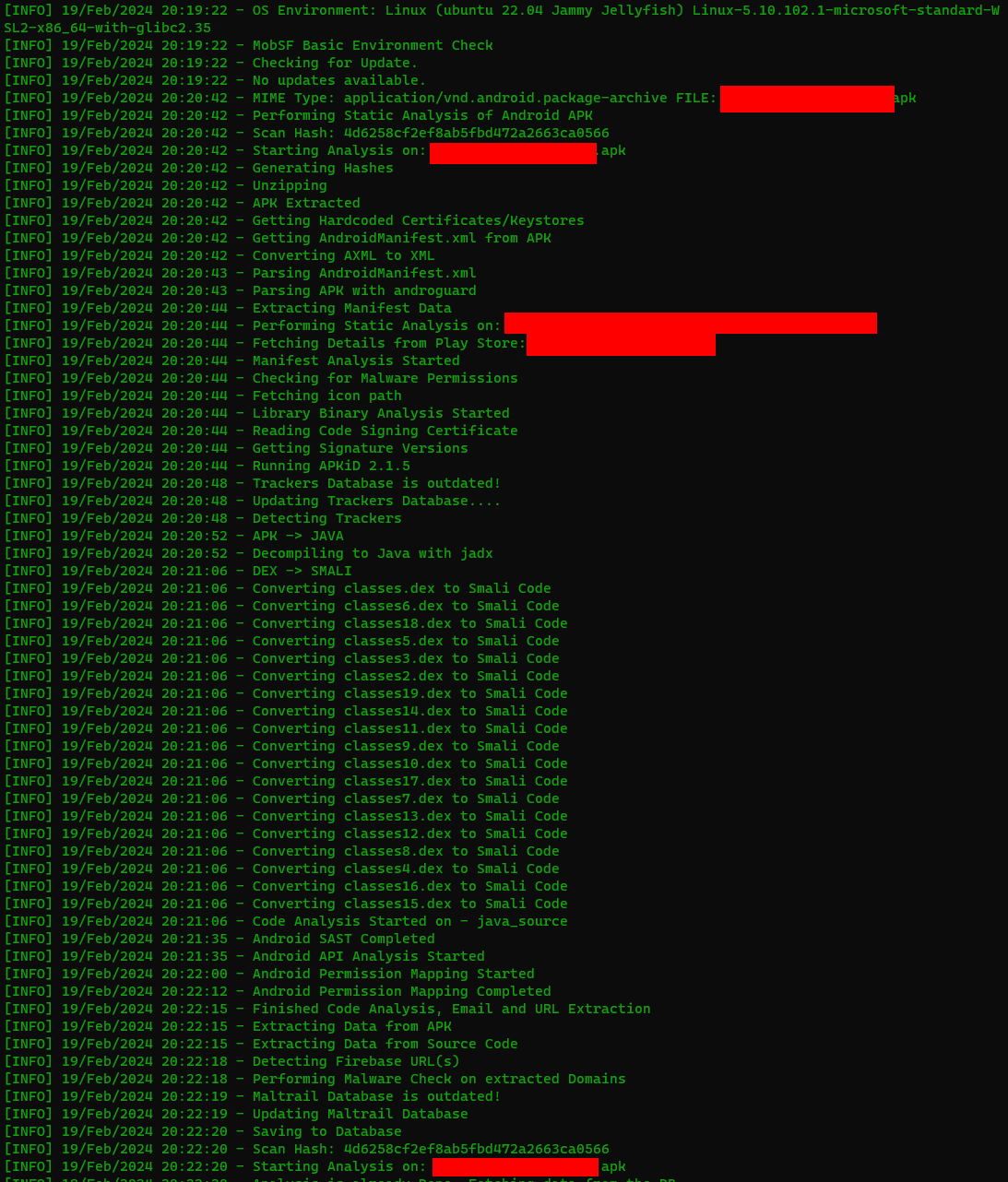
The dashboard has a lot of element concerning the APK. Scroll by way of to see the permissions it is using, certificates connected to it, potential safety vulnerabilities, code evaluation, detected URLs within the code, onerous coded secrets and techniques, and strings. All of those would assist a crew construct a greater and safer cellular software.
Conclusion
For my objective, this 15 minute excersice not solely answered the query I used to be searching for it additionally raised a couple of objects that can should be corrected earlier than the following launch. Introducing safety practices with a device like MobSF can be extremely benefitial to a crew tasked with constructing an Android software. Additional, including within the dynamic evaluation capabilities can present extra particulars on areas to enhance.
Whereas I did not want these to reply my query, I would enourage somebody seeking to introduce this to a crew, to take a look at the capabilities of MobSF

